1. The Key Expansion Part 1: RotWord
AES is a block cipher that can encrypt and decrypt no-more-no-less than 128 bits of plaintext. This limitation is usually circumvented by using a mode of operation along with a padding algorithm on top of a block cipher. But this is not important for us here, as we are aiming to attack the core of block ciphers, not their usage.
In addition of a 128-bit plaintext, AES also takes a variable sized key. In our attacks we will use AES-128 which uses, as its name suggests, a 128-bit key. But know that there exist two other variants of AES called AES-192 and AES-256, taking respectively 192-bit and 256-bit keys and having their implementation differ slightly from AES-128.
To transform a plaintext into a ciphertext, AES makes it undergo a number of transformations, one of them is to XOR it with keys. Since we only provide AES with a single key, AES will need to derive a number of keys from it. This number will vary accordingly to the version of AES you are using. Since we will use AES-128, we will need it to derive exactly 11 keys.
Let's name these concepts:
- these derived keys are called round keys (or commonly subkeys)
- the process used to derive these subkeys is called a key expansion (or commonly a key schedule)
We will create three different functions to help us build the KeyExpansion() function:
RotWord()SubWord()Rcon()
The first we will implement is RotWord. So open your IDE/text editor and implement a RotWord() function. It should take as input a value of 4 bytes and return as output a rotation of these 4 bytes as shown in the diagram below:
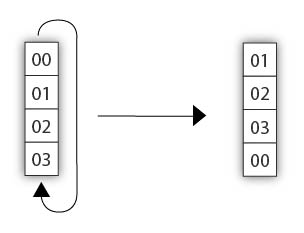
Test your function and make sure it works :) When you're done, go to the next step.